ActZero MDR overview
ActZero’s Managed Detection & Response (MDR) cybersecurity services work to protect your organization’s network, systems, and assets from malicious attack. A team of expert Threat Hunters help you remediate vulnerabilities and mitigate the risk of attack, and are prepared to offer immediate help to address a cybersecurity emergency.
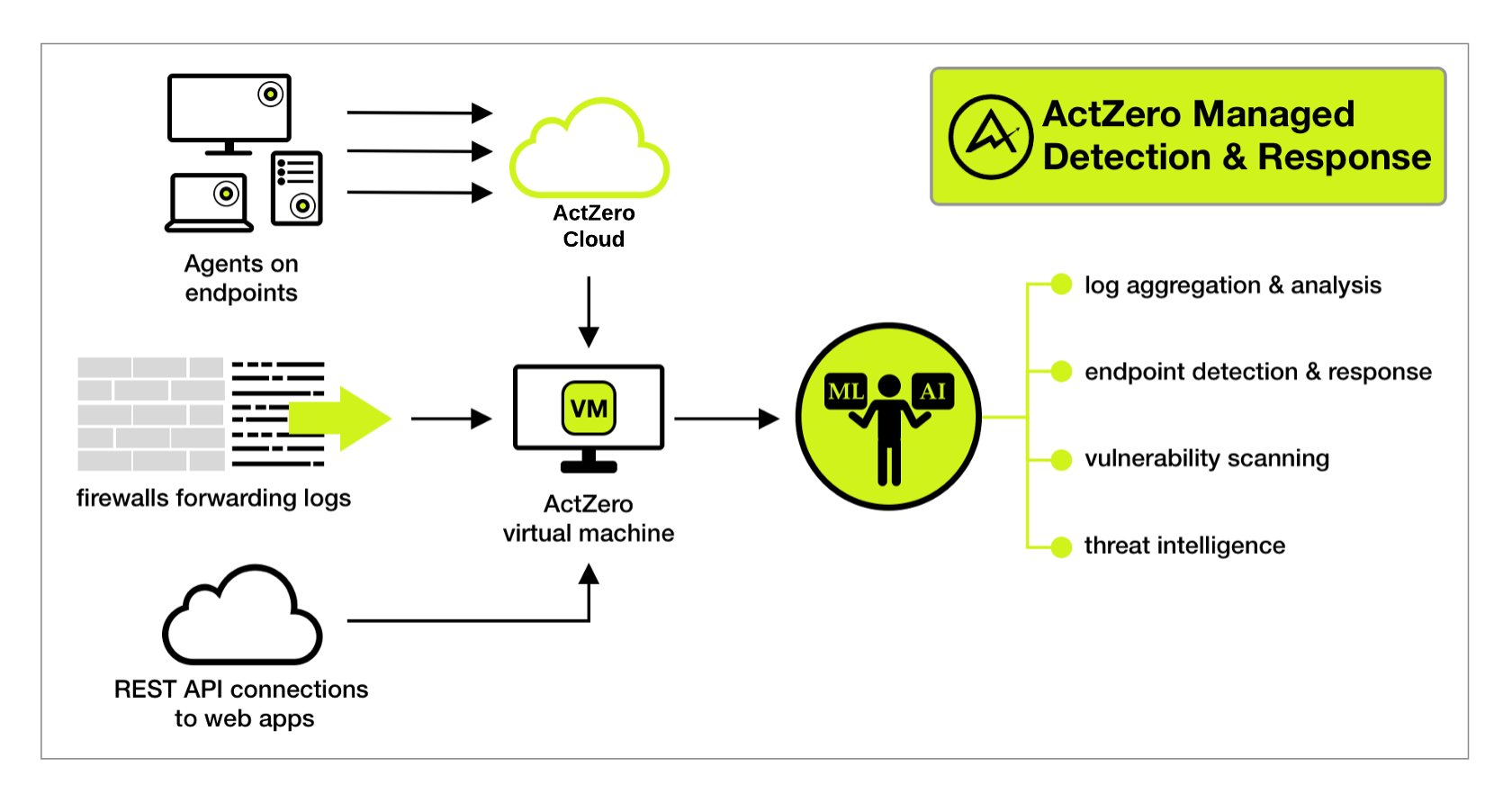
The scope of MDR services includes multiple approaches to find vulnerabilities in your network infrastructure, detect suspicious behavior, and respond in case of attack. The following overview offers insight into the work that ActZero does to keep your organization safe.
Log aggregation and analysis
Log files are files that record events and activity that occur in your system. ActZero collects and aggregates the information that your system’s software and tools log so as to analyze it for signs of suspicious activity.
There are a few types of events that ActZero monitors:
- system events on endpoints in your environment, such as user logins, script commands, and changes to application settings
- network events, such as URL filtering, and proxy gateway activity
- cloud-hosted web application events, such as web app logins, user activity, and user authentication
To capture the information associated with those events, ActZero uses several tools and methods to collect logs.
- agents on endpoints in your environment that collect system events
- firewalls configured to forward syslogs to collect network events
- REST APIs that collect web-application events
ActZero Threat Hunters leverage machine learning and artificial intelligence to aggregate and monitor activity in your organization’s network infrastructure. The team looks for signs of threats, such as:
- shell attacks, where an attacker executes arbitrary commands on a server or web application in an attempt to gain unauthorized access to other resources in the network
- brute force attacks, where an attacker attempts to log in to a user account using many passwords to try to guess the correct one and take over an account
- credential stuffing, where an attacker uses a leaked list of usernames and passwords to try to log in to accounts on multiple websites and applications in an effort to take over an account
- security scans, where an attacker uses automated tools, or BOTs, to discover vulnerabilities in a web application or network
- data exfiltration, where an attacker accesses a system to conduct an unauthorized transfer of data (login credentials, credit card numbers, personal information) from a resource in a network
Endpoint detection and response
An endpoint is a device or machine that is connected to your network. Some examples of endpoints are desktop computers, mobile devices, tablets, and servers. Endpoints can be vulnerable to attack as malicious actors use them as entry points into a network.
To monitor activity and mitigate the risk of attack, ActZero works with your IT administrator to install agents on endpoints in your network. These agents are programs that perform continuous, autonomous actions to monitor activity on an endpoint. ActZero has partnered with CrowdStrike, an industry-leading provider of endpoint detection and response (EDR) software, to use their endpoint agent software.
Using the endpoint agents, ActZero Threat Hunters can:
- quarantine endpoints to limit network activity
- terminate processes, scripts, or actions
- delete malware files that unsuspecting users installed
- extract malware files for further analysis
- run commands to reverse operations that malware performed, such as system modifications
Endpoint detection and response aims to guard against several kinds of attacks on your network or system, including:
- Trojans, where an attacker installs malware disguised as a legitimate program on a system
- ransomware attacks, where an attacker uses a Trojan or other malware to block access to systems or data until the victim pays a ransom
Vulnerability scans
ActZero takes proactive measures to detect cybersecurity vulnerabilities in your organization’s network and systems. One of the methods that Threat Hunters use to search for weaknesses is vulnerability scanning. This method takes a few forms:
- network scans that search for known and exploitable vulnerabilities on systems such as network switches, operating systems, and applications
- web application scans that look for vulnerabilities in the source code of web applications your organization developed
- compliance scans that audit system configurations and software for security and compliance, looking for out-of-date software, ill-configured settings, and weak encryption and password policies
ActZero Threat Hunters use the information these scans find to recommend steps you should take to address vulnerabilities in your network infrastructure.
Threat intelligence
ActZero Threat Hunters and Data Scientists leverage a machine learning (ML) and artificial intelligence (AI) engine to continuously and actively hunt for threats. In particular, the ML/AI engine they use performs several activities:
- searches for threats on full data sets, or data lakes, to find anomalies
- uses honeypots (disguised traps to catch attackers), sandboxed threat samples, and threat intelligence feeds to detect threats
- performs automated actions to mitigate threats
- automatically alerts Threat Hunters of issues to ensure timely responses to attacks
Information and advice
Beyond the active efforts of a team of Threat Hunters and the automated tools they use, ActZero offers your organization information and advice on how to harden your cybersecurity, optimize your defenses, and reduce your risk of attack.
- ActZero produces a monthly report for your organization that details the security-related activity the team monitored and recommends actions you should take to protect your network, systems, and assets.
- The ActZero customer portal enables you to access information about your organization’s security posture and empowers you to improve it. Log in to the portal to download your monthly report and review a Dashboard of recent security-related events.
- ActZero’s Virtual Chief Information Security Officer (vCISO) can answer strategic, technical questions and provide prioritized guidance for cybersecurity compliance and best practices.
If you do experience a breach or have an urgent security issue, the ActZero team of Threat Hunters is available to help:
- For any urgent security issues, call 1-855-917-4981.
- Contact ActZero with any non-urgent security issue or question about your service.
Go further
- Find out about how to get started with ActZero’s MDR services.
- Find out how to contact ActZero for help or advice.
- Learn more about ActZero vCISO services.
Was this documentation helpful? Please send us your feedback!