Configure AWS to connect to ActZero
Estimated Time to Complete: 10 minutes
Contact us to learn more about adding Managed Detection & Response (MDR) services to your AWS endpoints.
To enable the ActZero team to monitor your AWS environment, you need to complete a few steps to configure a connection from your cloud environment to ActZero. Use the instructions below to set up an AWS CloudTrail connector and add a new user with the necessary permissions.
For a list of prerequisites, please visit the Get started page.
As you go, be sure to collect the following pieces of information to securely share with ActZero:
- the name of your new S3 bucket
- S3 prefix path
Architecture Overview
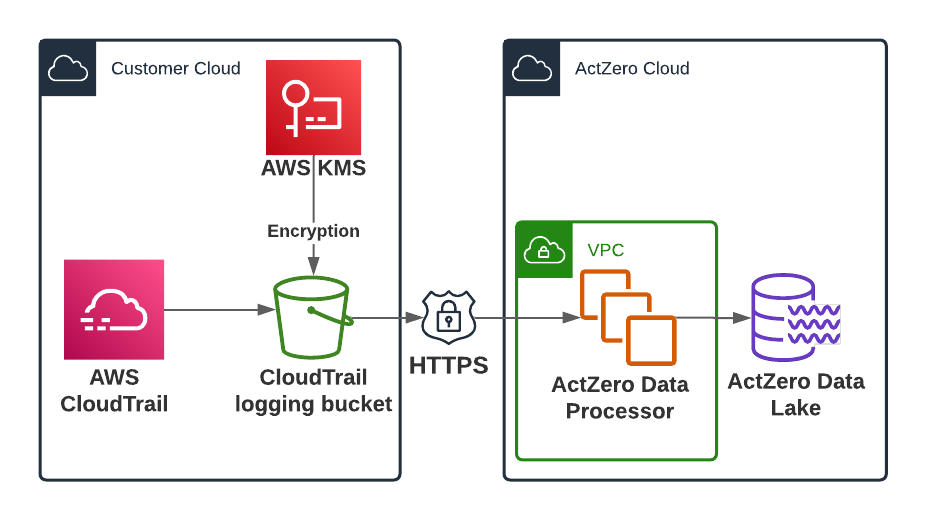
- The CloudFormation template will create a KMS Key that is used to encrypt the CloudTrail data in S3
- Once ActZero receives the data over a secure HTTPS connection, it will remain encrypted at rest
Run CloudFormation Automation
- Download the CloudFormation Template from the Actzero Gitlab Repository.
- Log in to your AWS Management Console.
- Use the Find Services search field to find and select CloudFormation.
- In the CloudFormation Dashboard, click Create stack, and choose with new resources (standard).
- Under Prerequisite - Prepare template, leave the default option Template is ready selected.
- Under Specify template, choose Upload a template file. Click Choose file and select the cloudtrail-config.yml file you downloaded in step 1, then click Next.
-
Enter a Stack name
-
If there is an existing CloudTrail you'd like to use, select "Yes" in the "CloudTrailExists" field and enter the name of that trail in the "CloudTrailName" field
-
If you'd like to create a new CloudTrail, select "No", enter a name for your trail, and click Next
-
-
On the Configure stack options page, leave all options as default, and click Next.
- Scroll to the bottom of the Review
page, and under Capabilities, click the button to acknowledge that CloudFormation may create IAM resources on your behalf, and then click Create Stack. - Within a few minutes, the automation will complete, which can be noted by the Status of the CloudFormation Stack.
Obtain CloudFormation stack outputs
- In the CloudFormation Dashboard, click on the newly created stack.
- Click the Outputs tab, and make note of the 2 Key and Value pairs, CloudTrailPrefix and CloudTrailS3Bucket
Obtain IAM credentials from AWS Secrets Manager (Optional)
-
If there is not an ActZero VM deployed in the AWS account where the CloudTrail was created:
-
Browse to the AWS Secrets Manager console
-
Click on the secret named
aws-cloudtrail-user-iam-keys -
Click the "Retrieve secret value" button
-
Use Keybase to securely encrypt and share the IAM credentials. You do not need to create a Keybase account.
-
Recipient: actzerocre
- Message to encrypt:
- access key ID
- secret access key
-
Share with ActZero
- Email the values of the CloudTrailPrefix and CloudTrailS3Bucket to your Technical Account Manager
Rotating IAM Keys
For security reasons, it is important to regularly rotate the IAM credentials that are generated by this process. For best practices and how-to guides, please reference the official AWS documentation.